I have usually always deployed always on vpn device tunnel as most of my customers just want to migrate 1:1 from direct access.
But lateley after migrating more and more customers to Endpoint Manager, I needed to do a change in the above approach and start to use User Tunnels because device tunnels cannot autodial when the machine is only azure ad joined.
Suddenly some customers start to complain that they cannot reach their fileserver only on the hostname, and they could do that on the device tunnel.
My investigation showed that everything was working as expected when I tried to ping the fileserver. I could rdp to the fileserver – but accessing the SMB-shares didn’t work.
After a lot of troubleshooting I finally found the solution on Richard Hicks blog. In case he changes something I will provide the fix here:
Solution 1
in %appdata%\Microsoft\Network\Connections there is rasphone.pbk. Open it with notepad;
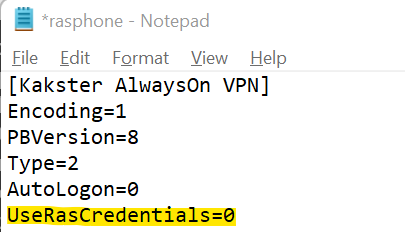
Change UseRasCredentials from 1 to 0.
Powershell Code;
$rasphoneFile = "$env:appdata\Microsoft\Network\Connections\pbk\Rasphone.pbk"
if(Test-Path -Path $RasphoneFile) {
try{
$rasphoneFileData = (Get-content -Path $rasphoneFile).Replace("UseRasCredentials=1","UseRasCredentials=0")
}
catch{
Write-Error "Failed to replace UseRasCredentials with error: $_"
}
}
else{
Write-Error "Rasphone PBK not found"
exit 1
}
If you are entitled to use Proactive Remediation Scripts in Endpoint Manager, Richard also comes to the rescue here and have created a Git Hub repository for that.
Here is the direct link to the detect script and the remediation script
If you just want to check out the entire repository here’s the link
Solution 2 – IMO the best solution
If your pc is hybrid joined you can use gpo to stop this;
Network access: Do not allow storage of passwords and credentials for network authentication
if you set this to enabled everything works.
It is located Computer Configuration\Policies\Windows Settings\Security Settings\Local Polices\Security Options
If you are manage the device with intune, yo do not have the above policies so you need to set it with registry;
Start-Transcript -path "$env:windir\logs\Software\AlwaysOnVpn-DisableCredentials.log"
$regPath = "HKLM:\System\CurrentControlSet\Control\Lsa"
$name = "disabledomaincreds"
try{
Write-Output "Trying to set regkey $regPath\$name"
Set-ItemProperty -Path $regPath -Name $name -Value 1
}
catch {
Write-Error "Failed to set registry key"
}
Stop-TranscriptWas this helpful please rate